How to Mitigate Log4j VMware Vulnerability – Workaround
In light of the recent Apache Software Foundation Log4j Java component vulnerability (CVE-2021-44228 and subsequent CVE-2021-45046) which may allow for remote code execution, many are looking to mitigate exposure. Due to the critical nature of the vulnerability, it is recommended mitigations are implemented immediately. Numerous companies and their applications use log4j to log information from Java-based software. VMware is just one of those companies that use the log4j Java component. As such, VMware recently released a critical security advisory (VMSA-2021-0028) addressing the situation. In its current developing state, VMware products have patches pending. However, VMware has released manual workarounds in the interim. Below we will walk through the workaround mitigation process for a vCenter Virtual Appliance (VCSA) 7.x utilizing the recommended Python script.
NOTE – CVE-2021-44228 and CVE-2021-45046 affects vCenter 7.0.x, 6.7.x, and 6.5.x. This workaround is a short-term solution as a patch is still being developed. Updates to VMSA-2021-0028 should be applied when available. This article has been updated to use the unified script. Previously, two scripts were needed (vmsa-2021-0028-kb87081.py and remove_log4j_class.py). If you only ran one of the scripts or would like to check if vCenter is vulnerable, run the unified script with the dry run flag (details below).
If are reading this article, check the VMware Advisory FIRST for updates before proceeding.
Prerequisites:
- vCenter High Availability (VCHA) needs to be removed before executing the steps.
- Python script needs to be executed on both vCenter and PSC appliances in environments with external Platform Services Controller (PSC).
How to Mitigate Log4j VMware vCenter Vulnerability – Utilizing Python Workaround
- Download the vc_log4j_mitigator Python script included in the vCenter workaround instructions.
- You can either copy the contents of the Python script via SSH or transfer the file using your preferred file transfer software (WinsSCP, Filezilla, etc.) to your VCSA. If using SSH, you will need to enable SSH on your vCenter (and disable when finished). If using file transfer, you will most likely need to enable the Bash shell. In our example, we will copy the contents via SSH.
- To copy via SSH, first enable SSH on vCenter. Do so by navigating to the vCenter Management Interface (VAMI) via https://vcenter_fqdn_or_ip:5480/.
- Once logged in, go to the Access tab and click the Edit Pencil.
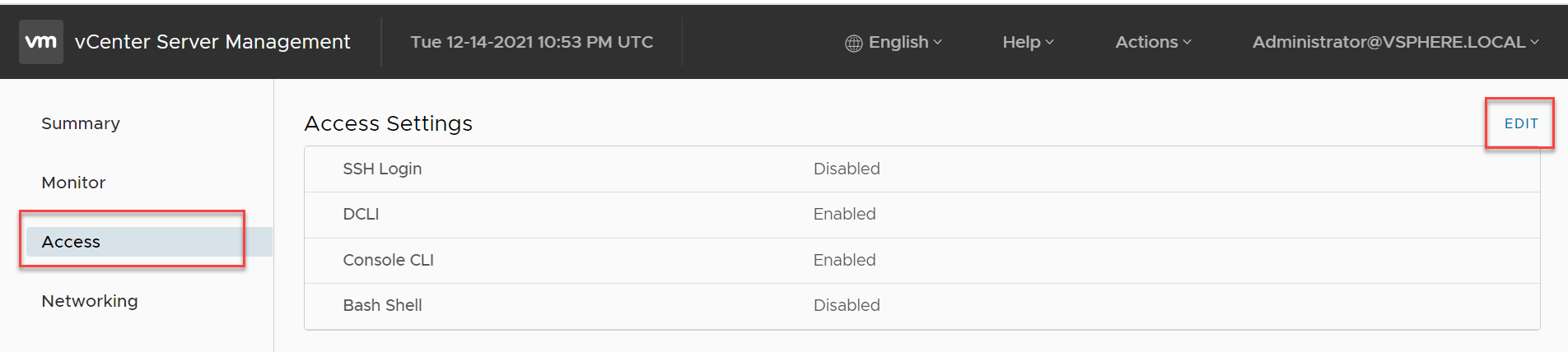
- Toggle on Enable SSH Login and click Ok.
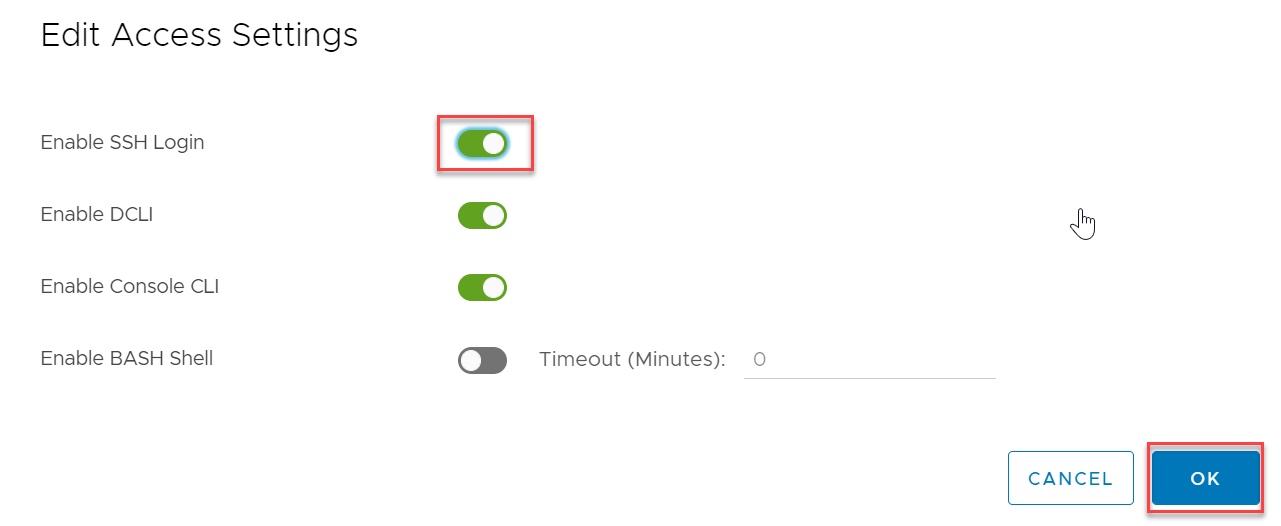
- Next, SSH to your vCenter appliance using PuTTY.
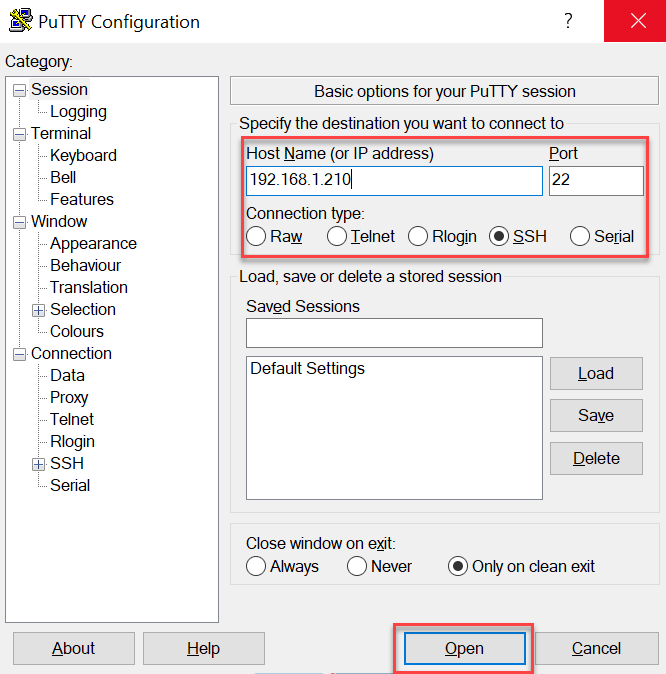
- Login with the pertinent credentials and launch shell.
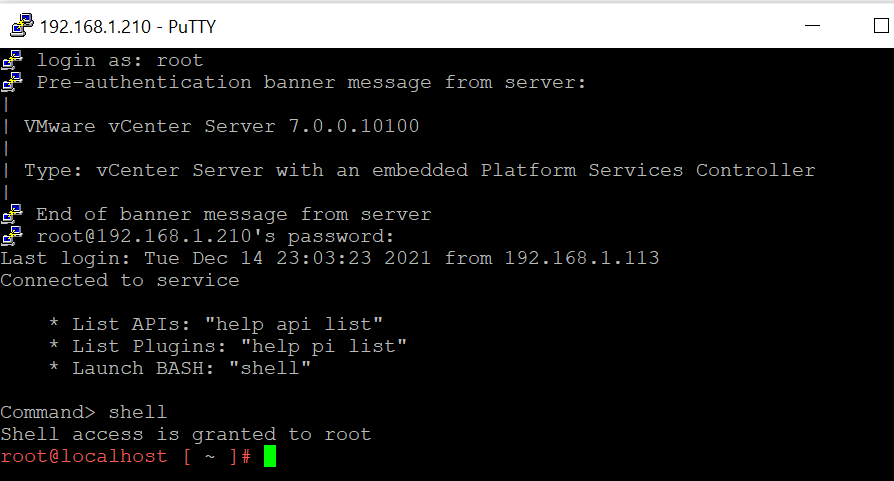
- Create a new file for the Python script utilizing the vi command: vi /tmp/vc_log4j_mitigator.py
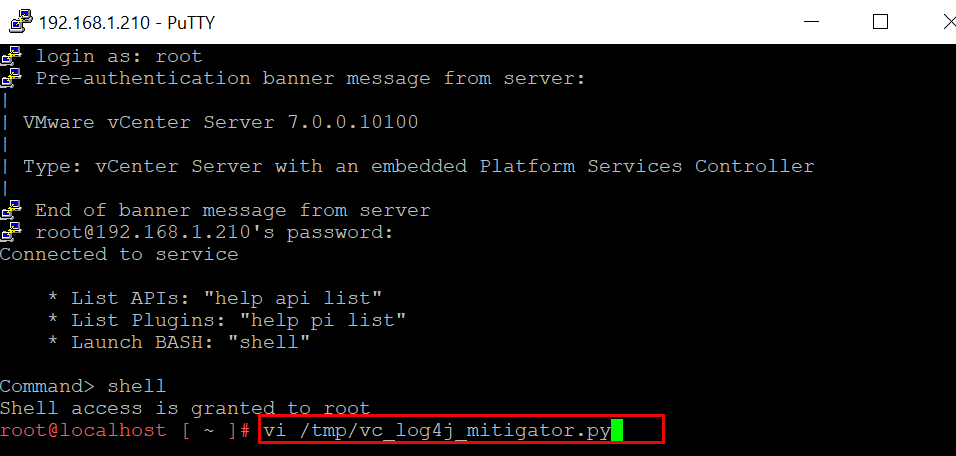
- Enter Insert mode to copy the Python script contents by pressing i

- Next, open the previously downloaded Python script with Notepad or Notepad ++ and copy all the contents.
- Navigate back to your SSH session and right-click in the console to copy the Python script contents.
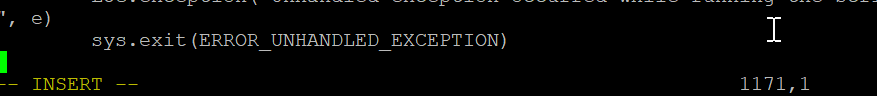
- To save the file and exit, hit the escape <ESC> key to enter back into normal mode and type :wq!

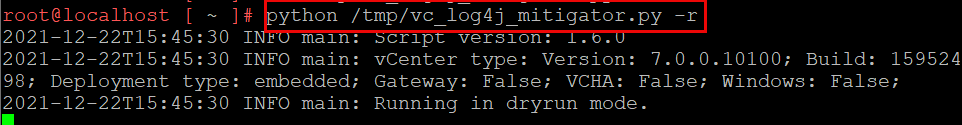
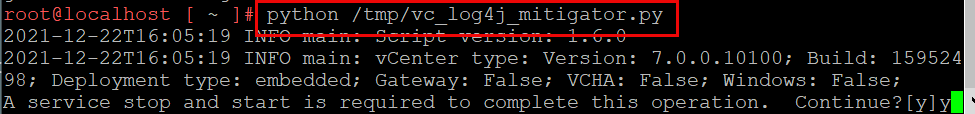
- Next, we can use the python script to check if vCenter is vulnerable. In our instance, we performed a previous workaround and are unsure if that provided adequate remediation. To do so, execute the script with the dry run flag: python /tmp/vc_log4j_mitigator.py -r
- This dry run will detect vulnerable files without mitigating them.
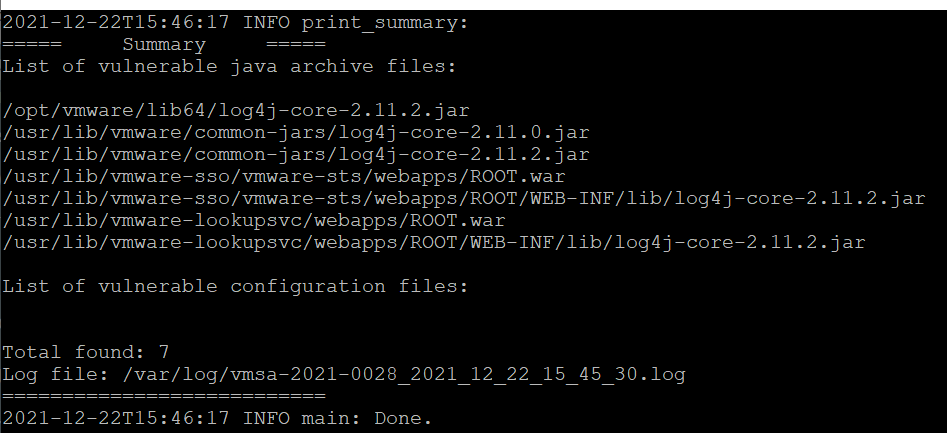
- As we still are vulnerable, we will execute the script without the dry run flag: python /tmp/vc_log4j_mitigator.py
- Upon execution, you will be asked to restart service. Enter Y to proceed.
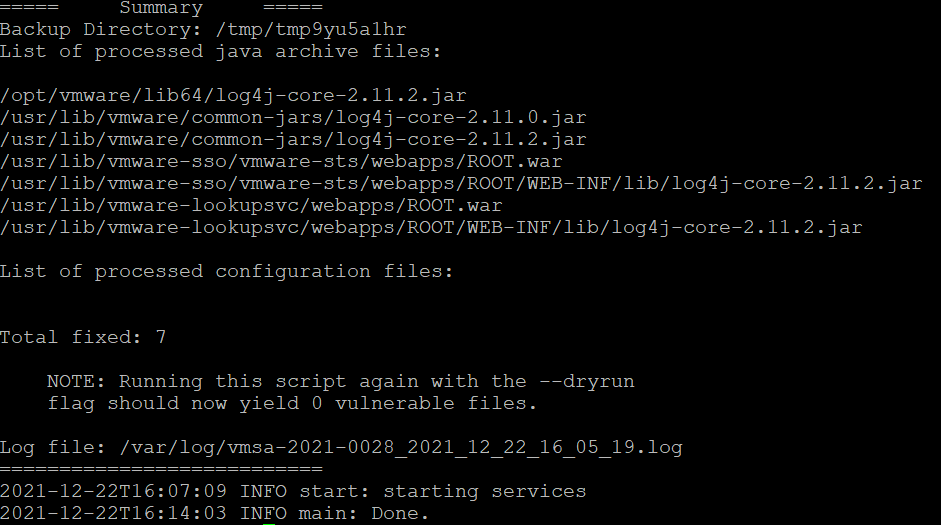
- Once the script completes (this may take a few minutes), a summary of fixed vulnerable files are shown.
- Lastly, ensure you go back to the VAMI and disable SSH.
Check back for tutorials on how to update VMware vCenter once a remediation patch has been released.